
Tech with Leens
Top Networking Interview Q&A | From Basics to Advanced (2025 Guide)
2:35

Tech with Leens
Routers vs Switches Explained | Key Networking Differences Made Simple
2:00

Tech with Leens
What is NAT? | Network Address Translation Explained Simply
2:21

Tech with Leens
What to Learn BEFORE Cybersecurity | Complete Beginner’s Roadmap
2:30

Tech with Leens
5 Simple Steps to Take If You’ve Been Hacked 🔒 | Cybersecurity Tips
2:13

Tech with Leens
Proxy server explanation in 2 minutes
2:02

Tech with Leens
The differences between dark and deep web #darkweb #deepweb #cybersecurity
0:19

Tech with Leens
Malware vs Virus vs Trojan #cybersecurity #cyberattacks
0:23

Tech with Leens
Dynamic IP vs Static IP #ccna #networkengineer #cybersecurity #ipaddress
0:19

Tech with Leens
IPv4 vs IPv6 #ccna #networkengineer #computernetwork
0:19

Tech with Leens
The differences between dos & DDOS attacks #cybersecurity #cyberattacks
0:20

Tech with Leens
The disadvantage of using VPN #vpn #cybersecurity #network
0:16

Tech with Leens
The differences between MAC and IP addresses #networkengineer #cybersecurity #computer
0:18
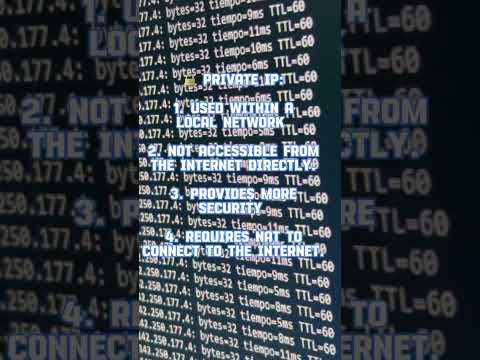
Tech with Leens
The differences between public and private IP addresses #networkengineer #ccna #cybersecurity
0:17

Tech with Leens
What’s privacy?
4:39

Tech with Leens
HTTP vs HTTPS #networkengineer #cybersecurity #computernetwork
0:18

Tech with Leens
The difference between symmetric & asymmetric encryption algorithms #networkengineer #cybersecurity
0:17

Tech with Leens
The difference between hashing and encryption #cybersecurity #networkengineer
0:17

Tech with Leens
The differences between TCP and UDP! #computernetwork #ccna #ccnp #networkengineer #cybersecurity
0:17

Tech with Leens
Types of privacy! #cybersecurity #networkengineer #computernetwork
0:16

Tech with Leens
What is the communication types? #ccna #networkengineer #computernetwork #ccnp
0:10

Tech with Leens
Most popular cyber attacks ! #cybersecurity #cyberattack #cyberattacks #facts
0:10

Tech with Leens
Cybersecurity activities #cybersecurity #cybersecuritysolutions #ethicalhacking
0:11

Tech with Leens
Cyber security roadmap for beginners. #cybersecurity #networksecurity #cybersecurityengineer
0:10

Tech with Leens
HSRP Configuration in Packet Tracer | Network Redundancy Lab (Step-by-Step)
3:40

Tech with Leens
5 Must-Know Cybersecurity AwarenessTips to Stay Safe Online
2:43

Tech with Leens
EIGRP Routing Protocol Configuration /Step-by-Step Cisco Tutorial
0:15

Tech with Leens
EIGRP Routing Protocol Configuration |Step-by-Step Cisco Tutorial
3:25

Tech with Leens
Certifications That ACTUALLY Matter for Network Engineers
0:09

Tech with Leens
How to keep our kids safe online!
3:08

Tech with Leens
OSPF Configuration 101: A Beginner's Guide
4:13

Tech with Leens
Master the Security Incident Lifecycle:Step-by-Step Guide to Cyber ThreatResponse
5:54

Tech with Leens
Get Started with RIP in Cisco PacketTracer! #RIPRouting #CiscoPacketTracer #CCNATutorial
0:09

Tech with Leens
What Are Social Engineering Attacks? How to Identify and Prevent Them
5:51
Tech with Leens
Get Started with RIP: Easy Configuration in Cisco PacketTracer!
5:13

Tech with Leens
6 Key Techniques in Ethical Hacking
5:16

Tech with Leens
What is Cloud Computing? Simple Explanation for Beginners
4:32

Tech with Leens
Beginner’s Guide to Basic Router & Switch Configuration | Step-by-Step with Free Config Guide!
4:56

Tech with Leens
What is the internet protocol?
2:46

Tech with Leens
The CIA triangle in cybersecurity
3:35

Tech with Leens
Explanation of SMTP? | Simple Mail Transfer Protocol
3:40

Tech with Leens
The difference of white gray and black hat hackers!
7:48

Tech with Leens
VPN explanation | what’s the VPN?
3:18

Tech with Leens
The explanation of the DNS
3:32

Tech with Leens
Cryptography; hashing and encryption explanation!
4:02

Tech with Leens
How DHCP works?
3:30

Tech with Leens
What is the DHCP? & why is it important?
3:29





