
Chris Pirillo
What is TippingPoint Secure Virtualization Framework?
14 years ago - 7:36

UW Video
Secure Virtualization with Formal Methods
12 years ago - 51:18

eWEEK.com
Daily Tech Briefing: VMware Developing Ways to Use Encryption to Secure Virtualization
10 years ago - 3:10

Oracle Linux
Simple and Secure Virtualization for your Datacenter
5 years ago - 5:41

Back From The Ether
zyLabs CompTIA Security+ Lab : Secure Virtualization (Walkthrough) - 050824R01
11 months ago - 13:15

Julissa Bethard
What is TippingPoint Secure Virtualization Framework
11 years ago - 7:34

Code in Action
SELinux System Administration, Third Edition | 9. Secure Virtualization
5 years ago - 23:25

Omnistruct
Next-Gen Secure Virtualization: Market Trends And Insights In Cybersecurity With Brad Sollar
2 years ago - 33:28

NC State ECE
NC State Faculty Members Awarded Funded Research for Secure Virtualization
4 years ago - 6:07

Purdue CERIAS
2007-10-24 CERIAS - Secure Virtualization
13 years ago - 1:02:27
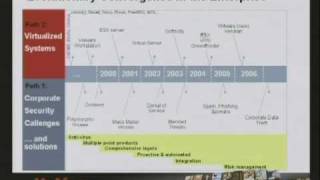
Christiaan008
CERIAS Security: Secure Virtualization 1/7
15 years ago - 9:59

Tom Olzak
Secure Virtualization
3 years ago - 10:31

CBT Nuggets
5 Ways to Protect Virtualized Systems
3 years ago - 10:49

Christiaan008
CERIAS Security: Secure Virtualization 7/7
15 years ago - 2:35

congatec
Operating Systems on aReady.COM - KontronOS
4 weeks ago - 0:43

The Linux Foundation
Putting Together a Secure Virtualization and Containerization Platform - Stéphane Graber, Zabbly
5 months ago - 46:36

Christiaan008
CERIAS Security: Secure Virtualization 3/7
15 years ago - 9:59

ntegral
Cloud Managed Maria DB 10 on Ubuntu 22.04 | Fast & Secure Virtualization
Streamed 2 years ago - 18:54

CyberMuk
2.3 - Virtualization Vulnerabilities (CompTIA Security+ SY0-701)
1 year ago - 4:35

SAE International
How to Address the Existing and Future Requirements of ASFC: The Safe and Secure Virtualization...
13 years ago - 1:03

The Linux Foundation
Secure Virtualization for MCUs Using Wasm - Toni Bofarull, Midokura (Sony Group)
2 years ago - 34:30

Rob Braxman Tech
Why Use Virtual Machines for Privacy and Security? Not Obvious! Top 6 List!
1 year ago - 19:45

Citrix Ready
Guardicore: Enabling Business Continuity with Secure Virtualization
Introduction ...
5 years ago - 1:02:04

Microsoft Learn
Manage Hyper-V virtualization in Windows Server AZ-800 | Episode 6
1 month ago - 49:15

Microsoft Events
Unlock the full power of Windows 365 | BRK343
4 weeks ago - 43:45

The Linux Foundation
Keynote: Retrospective: 26 Years of Flexible MAC - Stephen Smalley, National Security Agency
6 years ago - 58:43

Proof-of-Work Summit
Mining is Critical Infrastructure + Enables Sovereignty - Ryan Lackey
1 year ago - 59:25
![How to Activate Parallels Desktop 26 for Mac [2025] - Official Parallels Desktop Activation Key](/vi/z7HRjWGAkEE/mqdefault.jpg)
Crypto recovering
How to Activate Parallels Desktop 26 for Mac [2025] - Official Parallels Desktop Activation Key
2 months ago - 0:17

SUSE
KubeCon 2024: Kubernetes Security Trends with Mainsail
10 months ago - 3:54

Red Hat Summit
Understanding security risks and mitigation across the virtualization stack
9 years ago - 31:30
Al Amin Facts ⭐
9 Cloud Computing Security Best Practices,cyber security in cloud computing
2 years ago - 3:11

avastofficial
avast! Internet Security Sandbox - Virtualization
15 years ago - 0:46

Trimarc Security
Webcast - Saving The Marriage-AD & vSphere Happily Ever After
2 years ago - 1:07:12

Citrix Ready
Citrix and Guardicore, better together
5 years ago - 2:56