Professor Messer
Authentication, Authorization, and Accounting - CompTIA Security+ SY0-701 - 1.2
2 years ago - 9:04

Microsoft Azure
Authentication fundamentals: The basics | Microsoft Entra ID
6 years ago - 4:33
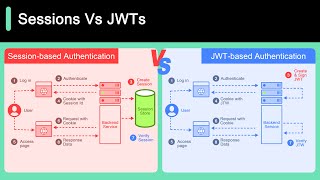
ByteByteGo
Session Vs JWT: The Differences You May Not Know!
1 year ago - 7:00

Google Career Certificates
Security: Authentication, Authorization, and Accounting | Google IT Support Certificate
4 years ago - 50:14

ByteByteGo
OAuth 2 Explained In Simple Terms
2 years ago - 4:32

Hayk Simonyan
Authentication Explained: When to Use Basic, Bearer, OAuth2, JWT & SSO
6 months ago - 6:04

Devoxx
Authorization in Spring Security: permissions, roles and beyond by Daniel Garnier Moiroux
4 months ago - 2:49:21

Ro James XIX
Ro James - Permission (Official Video)
10 years ago - 4:42

LearnThatStack
API Authentication Explained (Finally) — Basic Auth, Bearer & JWT
3 months ago - 13:22

Fireship
Session vs Token Authentication in 100 Seconds
5 years ago - 2:18

ByteMonk
API Authentication: JWT, OAuth2, and More
1 year ago - 6:12

SoftsWeb
API Authentication EXPLAINED! 🔐 OAuth vs JWT vs API Keys 🚀
11 months ago - 9:42

xplodivity
Authentication vs Authorization Explained
2 years ago - 3:41

Interview Pen
Design a Simple Authentication System | System Design Interview Prep
2 years ago - 17:22

Jeremy's IT Lab
REST API Authentication | CCNA 200-301 Day 61 (part 2)
1 year ago - 29:15

Auth0
A Developer's Guide to Fine-Grained Authorization (FGA)
8 months ago - 12:23

NBC News
Insurance companies announce changes to prior authorization process
7 months ago - 1:46

Auth0
How does machine to machine authorization work? And, how to use it in Auth0 (M2M)
9 months ago - 8:32

Writing Practices
How To Write An Authorization Letter Step by Step Guide | Writing Practices
2 years ago - 8:11

Aaronx UG
Aaronx - Permission
7 months ago - 3:13

Keeper Security
The Different Types of Authorization Models
8 months ago - 1:43

Write & Make
Authorization Letter for Giving Permission Sample | How to Write Authorization Letter Writing
2 years ago - 4:44

CodeOpinion
Authorization: Domain or Application Layer?
9 months ago - 8:56

Professor Messer
Authorization, Authentication, and Accounting - CompTIA Network+ N10-007 - 4.2
7 years ago - 12:03

Microsoft Azure
Authentication fundamentals: Federation | Microsoft Entra ID
6 years ago - 6:19

Theo - t3․gg
The State of Authentication
1 year ago - 1:03:23

Mick Gordon
Mick Gordon - 07. Authorization; Olivia Pierce
9 years ago - 2:24

CodeSnippet
Spring Security Authorization Architecture Explained 🔒 | Roles & Permissions Deep Dive
8 months ago - 17:17

Sriniously
8. Authentication and authorization for backend engineers
1 year ago - 1:35:57

iAssist
How to make an authorization letter. #shorts #authorizationletter
3 months ago - 0:16

Michelle The Bartender
why some bars do a pre-authorization when you open a tab #bartender 
1 year ago - 1:12

Cloud Champ
Authentication vs Authorization Explained in 1 min! #devops #software
6 months ago - 0:48

Jay & Sharon
How to Ask for Permission #lifehacks
11 months ago - 0:15

Medicare School
Understand Medicare “Pre-Authorizations” in 60 Seconds
3 years ago - 0:43

Professor Messer
Authentication Methods - CompTIA A+ 220-1102 - 2.2
3 years ago - 6:16

LearnIT
Cookies vs Sessions for Authentication – Which is Better? | Web Security Explained
1 year ago - 0:44

athenahealth
Authorization Management | video | athenahealth
4 years ago - 1:55

Etactics
An Ultimate Guide to Prior Authorizations
11 months ago - 4:15

Insider
How CIA Black Ops Actually Work | Authorized Account | Insider
2 weeks ago - 57:42

CyberPlatter
What is Identification, Authentication, Authorization, Auditing, Accountability| IAAA| Cybersecurity
2 years ago - 9:56

Patrick God
JWT Authentication with .NET 9 🚀 Full Course with Roles, JSON Web Tokens & Refresh Tokens
1 year ago - 1:13:38

Corey Schafer
Python FastAPI Tutorial (Part 11): Authorization - Protecting Routes and Verifying Current User
3 days ago - 38:24

Availity
Automated Prior Authorizations: Understanding the Three Key Steps
8 years ago - 1:47

Insider
How Witness Protection Actually Works | Authorized Account | Insider
4 months ago - 31:04

Gaurav Sen
Zanzibar: Google’s Consistent, Global Authorization System
1 year ago - 17:02

The Cyber Mentor
Broken Object Level Authorization (BOLA) Explained
3 years ago - 8:06

Insider
How Mercenaries Actually Work | Authorized Account | Insider
4 months ago - 42:05

Auth0
Permissions, Privileges and Scopes - What's the Difference?
4 years ago - 13:30

Oso
Ten Types of Authorization
1 year ago - 51:02

Firebase
What is Firebase Authentication?
4 years ago - 13:22

Piyush Garg
Authorization in NodeJS
3 years ago - 19:33

MockInterviewPro
Top 5 Prior Authorization Specialist Interview Questions with Example Answers
8 months ago - 6:15

AHCCCSgov
Submitting a Prior Authorization Request Using the AHCCCS Online Provider Portal
5 years ago - 5:36