
L!NK
What Are Exploit Kits?
10 years ago - 12:58

Radware
What You Need To Know About Exploit Kits | Radware's 2019 Hacker's Almanac
6 years ago - 1:17

Sourcefire
Exploit Kits: An Overview
12 years ago - 1:51

RSA Conference
Quick Look: Exploit Kits and Malware ROI
7 years ago - 5:27

Bobby
Understanding Exploits and Exploit Kits
10 months ago - 6:36

RSA Conference
Exploit Kits, Malware ROI & The Shift in Attack Vectors
6 years ago - 34:26

Sunny Wear
Exploit Kits: The Biggest Threat You Know Nothing About
8 years ago - 17:23

BSidesIowa
BSidesIA 2017 Keynote: Exploit Kits and Indicators of Compromise – Brad Duncan
8 years ago - 55:26

Sourcefire
Web Exploit Kits (Part 1): Overview
12 years ago - 11:13

All Hacking Cons
Exploit Kits Hunting The Hunters Nick Biasini
2 years ago - 51:21

Pluralsight
Course Preview: Advanced Malware Analysis: Combating Exploit Kits
9 years ago - 1:19

SecPgh
Malware and Exploit Kits: Together Forever?
8 years ago - 40:26

VLR Training
What is Angler Exploit Kit cyber security terminology#cybersecurity #vlrtraining #education
8 months ago - 0:44

Cyber Siege
The Unseen Threat: Exploit Kits in Cyber Warfare
4 months ago - 0:48

botconf eu
Tracking Exploit Kits - John Bambenek
8 years ago - 44:48

ExploitKit
@ExploitKit subscribers

Sekoia Lab'
Exploit Kits Krawler Framework - Demonstration
11 years ago - 2:20

Kaspersky
Exploit Kits Evolution - Server Side
13 years ago - 7:28

Joey Muniz
How To Reduce Risk From Exploit Kits and Ransomware in K 12 August 10th 2016
8 years ago - 56:53

Adrian Crenshaw
Super Bad03 Exploit Kits Machine Learning Patrick Perry
8 years ago - 25:53

Adrian Crenshaw
202 Hunting for Exploit Kits Joe Desimone
8 years ago - 36:21
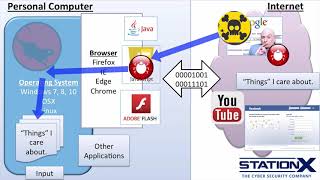
![OVERVIEW : EXPLOIT KITS [ ANGLER EK ]](/vi/j1aBqoPine4/mqdefault.jpg)
XPSTECH
OVERVIEW : EXPLOIT KITS [ ANGLER EK ]
9 years ago - 6:37

Kaspersky
Lab Matters - ROP Techniques in Exploit Kits
14 years ago - 8:28

ANOMALI
Exploit Kits Are Dead—Long Live Exploit Kits: Detect ‘18 Presentation Series
5 years ago - 48:19

Malwarebytes
Exploit kits: Winter 2017 review
8 years ago - 4:47

Information 14
Exploit Kits and Ransomware in State & Local Governments & Education
8 years ago - 52:26

Sourcefire
Web Exploit Kits (Part 2): Technical Description
12 years ago - 11:45

Veezo
ExploitKit explained by Veezo
5 years ago - 1:18

BSidesLV
BG - From EK to DEK: An Analysis of Modern Document Exploit Kits - Joshua Reynolds
5 years ago - 39:41

Hackfest Communication
Exploit Kits: The Biggest Threat You Know Nothing About (Sunny Wear)
8 years ago - 20:08

Veezo
ExploitKit expliqué par Veezo
5 years ago - 1:19

BSides Calgary
Mike Carlson: Becoming more intimate with Exploit Kits
4 years ago - 52:57

Adrian Crenshaw
I Got You05 Exploit Kits and Indicators of Compromise Brad Duncan
8 years ago - 48:38

Peter Schneider
Security: Why do exploit kits use droppers?
5 months ago - 2:15

Securelist
Lab Matters - Exploit Kits Evolution - Server Side
13 years ago - 7:28

Securelist
Lab Matters - ROP Techniques in Exploit Kits
14 years ago - 8:28

I'M Hacker
Darknets Dark Markets and Exploit kits / I'M Hacker |#cybersecurity #2022 #iamhacker
2 years ago - 8:05

CEH Courses
024 Darknets Dark Markets and Exploit kits
6 years ago - 8:05

All Safe
Darknets Dark Markets and Exploit kits
8 years ago - 8:05

Trustwave
From Black Hat: Anat Davidi, SpiderLabs Research Manager, on Exploit Kits and Ransomware
8 years ago - 7:49

Corey Nachreiner
Exploit Kits Spread Flash 0day - Daily Security Byte EP.106
10 years ago - 1:27

Virus Guides
The Rebranded Version of CryptoMix Called CryptoShield 1.0 Uses Exploit Kits
8 years ago - 1:05

Philippe Delteil
Super Bad03 Exploit Kits Machine Learning Patrick Perry
5 years ago - 25:53

CERT Polska
D1S1 John Bambenek Digital Surveillance on Exploit Kits EN
8 years ago - 40:18

Joe Concannon
RSA F.A.R.L.: What are Exploit kits 12 21 11
13 years ago - 3:59

Pankaj Pal
Hacking Tutorial | 025 Darknets Dark Markets and Exploit kits.mp4
6 years ago - 8:05

John Pole
exploitkit hacking
8 years ago - 0:16
T FLIX
024 Darknets Dark Markets and Exploit kits
4 years ago - 8:05

Slayer
exploitkit (Read description for appealing)
8 years ago - 0:08

All Hacking Cons
202 Hunting for Exploit Kits Joe Desimone DerbyCon 6
3 years ago - 36:21

This Week in Malware
TWIM Episode 10: STOP/Zorab Ransomware, Ursnif Malware, Angler/Nuclear Exploit Kits Tricks Victims
5 years ago - 11:49

Adrian Crenshaw
Offense03 The Economics of Exploit Kits E Crime Adam Hogan
9 years ago - 1:21:31

vmkr123
30+ Working Exploit Kits I Found (download link included)
15 years ago - 0:58

BSidesAugusta
Brad Duncan - Exploit Kits and Indicators of Compromise
8 years ago - 48:38

Sourcefire
Web Exploit Kits (Part 3): Thwarting Detection
12 years ago - 11:14

BSidesSLC
BSidesSLC 2015 -- Trends In Exploit Kits -- Jeffrey Doty
10 years ago - 54:31

Security BSides Dublin
Moving Away From Exploit Kits: The State Of Drive-By Downloads by Krishnan Subramanian
4 years ago - 25:52

All Hacking Cons
Hackfest 2016 Sunny Wear presented Exploit Kits The Biggest Threat You Know Nothing About
2 years ago - 20:08

Black Hat
Exploit Kit Cornucopia
7 years ago - 45:09

Philippe Delteil
I Got You05 Exploit Kits and Indicators of Compromise Brad Duncan
5 years ago - 48:38

GadgetsAndMore
Cyber Security || 12. Darknets, Dark Markets and Exploit kits
5 years ago - 8:02

MINIaSLAY
exploitkit and Insert teaming
8 years ago - 0:52

Pro🌟 Spammer
💥OG BOT version Exploitkit @professional_spammer11
2 years ago - 1:44

Info Con
#HITB2016AMS D1T1 - Exploit Kits Hunting The Hunters - Nick Biasini.mp4
7 years ago - 51:21

zero1080pZ
Top Leaked and Cracked Exploit Kits with download link (HD)
11 years ago - 3:23

Thomas Carlson
persamaan antara rootkit dan exploit kits adalah plis dibutuhkan sekarang dibuat singkat padat dan …
5 months ago - 0:51

BrakeSec Education
2016-016-Exploit Kits, the "Talent Gap", and buffer overflows
1 year ago - 1:00:14

Sam Bowne
DNS Security 101
6 years ago - 54:40

Tech Sphere
The Most Dangerous Hacker Tools Ever Made
3 months ago - 1:09

PAGEFIST official
🚀 Uncover the Dark Side of GitHub: Hackers' Playground 🚀 #GitHub #Cybersecurity #Hackers
1 year ago - 0:12

Philippe Delteil
BSides Salt Lake City 2015 BSidesSLC 2015 Trends In Exploit Kits Jeffrey Doty
5 years ago - 54:31

Saibentos
3 Hacking Tricks You Should Know in 2024!(@Saibentos )
1 year ago - 1:47

Cyber Defentech
Ever wondered what dark tools hackers use ?
1 month ago - 0:12

SecurityFirstCorp
How Criminals Start Ransomware Attacks? - SecurityFirstCorp.com
11 months ago - 2:15

SecurityFirstCorp
What Is Exploit In Security? - SecurityFirstCorp.com
7 months ago - 2:52

Black Hat
Next-Generation of Exploit Kit Detection By Building Simulated Obfuscators
8 years ago - 22:41

VPNRanks
The Hunt for the $2.5 Million Cybercrime Reward
11 months ago - 1:00

Ethical Echelon
OSI Model Explained in 60 Seconds! #cybersecurity #ethicalhacking #digitalsecurity #techtips #cyber
4 months ago - 1:00

Berlin Tech
"The Prize Email… Is a Trap!" #foryou #hack #cybersecurity
2 months ago - 0:21

SecurityFirstCorp
How Does Ransomware Get Installed? - SecurityFirstCorp.com
11 months ago - 2:03

molly
Mo11ly.exe website showcase
10 months ago - 0:36

cyber zee
exploit kit #ethicalhacking #2024 #trending
1 year ago - 6:58































![OVERVIEW : EXPLOIT KITS [ ANGLER EK ]](/vi/j1aBqoPine4/mqdefault.jpg)
































































